Cyber Security is an emerging area of concern for financial management information systems (FMIS) worldwide. These platforms may not only carry information on the aggregate budget and financial operations of the government but on individual citizens, such as tax data or cash transfers. Protecting this information through cyber security systems is important both for policy makers, practitioners and citizens themselves.
In this context, important lessons can be learnt from the ISO 27001 certification of the Public Financial Management System (PFMS) – India’s FMIS system. ISO 27001 is a global standard for Information Security Management Systems (ISMS). It is a technology neutral, process focused standard. In fact, the standard is as much applicable to PFM systems using pen-and-paper transactions as it is to digital PFM systems. However, its significance for digital systems in present times cannot be overstated.
Important lessons are as follows –
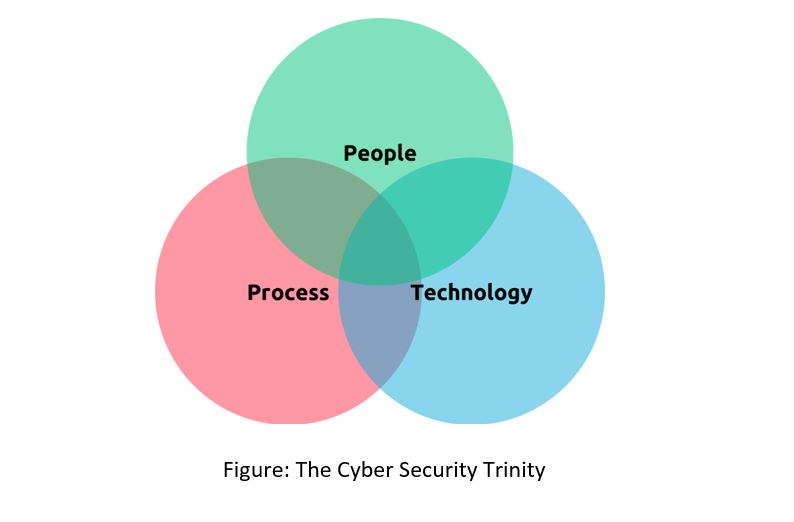
- All solutions do NOT lie in technology. Cyber security is not all technical (see chart below). Very often, among the trinity of people, processes, and technology, technology attracts the most attention. But people and processes are critically important. The strongest passwords are useless if shared. The strongest firewalls break down in case of an insider attack. The costliest security appliances require maintenance and eventual renewal. The easiest and simplest tasks can go haywire with a multitude of persons working on them unless processes are standardized. The list can go on.
- Ownership and leadership are essential. Cyber security debates often bring into sharp focus the dilemmas between efficiency and security. Adding another control, another layer of authentication, another encryption, another record/register, another management review – all add to security requirements but are also inversely related to the speed, ease-of-use and performance of the system. Adding too many control layers can reduce the acceptability of the system among the users who may prefer to go back to a physical paper-based system.
In such scenarios, a clear message from the top can help soften the resistance that comes when essential controls and new processes are enforced. Leadership provides vision and serves as a role-model to the whole staff. Similarly, only unwavering support from leadership can bring the necessary resources to cyber security which, in accounting terms, is a cost-center.
- Follow a structure/framework. The Weberian vision of bureaucracy being driven by a set of formal rules and provisions applies to cyber security systems and procedures. The US National Institute of Standards and Technology (NIST) framework outlines five core functions for cyber security – Identification, Protection, Detection, Response, and Recovery, each one carrying a detailed list of essential controls. For example, having a business continuity plan without adequate attention to access control or strong log analytics for anomaly detection without outlining the policy to respond to an incident – are mired with vulnerabilities. Conformity with internationally accepted standards goes a long way to enhancing the security of FMIS platforms and providing much needed assurance to the stakeholders.
- Understand the organizational context. It’s a common refrain that “every organization is unique”. That is easier said than practiced. All organizations work within a specific context. This context reflects their practices, work culture, risk appetite, technical architecture, reporting structures, and operational rules and protocols, if any. The ISO 27001 standard is strongly embedded in organizational context and must be well understood by the organization’s own staff. A cyber security policy which has been formulated with little comprehension of organization context and little involvement of internal stakeholders will have little ownership and be hard to implement.
- Policy on data archiving is important but challenging. Data archival has demanding challenges of balancing efficiency with the principle of data minimization. Holding large amounts of data may be tempting for analytical purposes but adds to the risk of securing the information. Similarly, the collection of data for analytical purposes, beyond what is required for essential operational purposes, must comply with privacy rules and regulations. Thus, an awareness of cyber security issues (both technical as well as legal-regulatory) is essential for functionaries whether they are part of a ministry’s IT/cyber security team or not.[1]
- Fail and fail faster and be open about it. Handling the pressure of initial hiccups in policy implementation is arguably a truth all practitioners must face once or more in their lifetime. Cyber security is no different. Engaging with operational teams to discuss challenges and spread awareness of cyber security provisions is essential, as is the humility to accept that the initially drafted cyber security policies and regulations may need revision. These policies must be given time to evolve without losing an organization’s focus and commitment to cyber security.
[1] A recently published IMF Technical Note on “Digital Solutions Guidelines for Public Financial Management”, provides guidelines on data archival and storage, data exchange and interoperability, and analytical capabilities. These aspects can have strong implications for cyber security.